Select the source of encryption keys (memory dump or hiberfil.sys) and encryption type (BitLocker, PGP or TrueCrypt/VeraCrypt) and press Next:
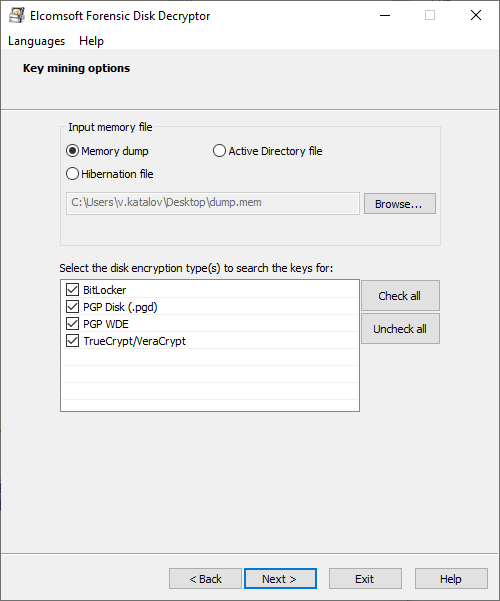
You van also select Active Directory (ntds.dit file) as a source; at this time, AD is only supported for BitLocker recovery keys.
Once the process is completed, the list of keys will be displayed. You can save them to a file for further use.
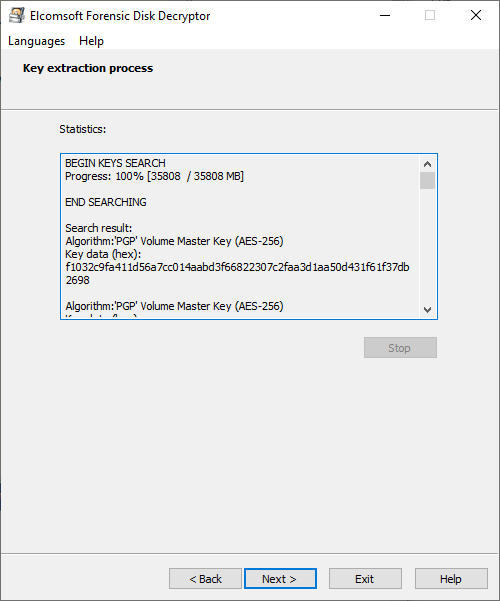
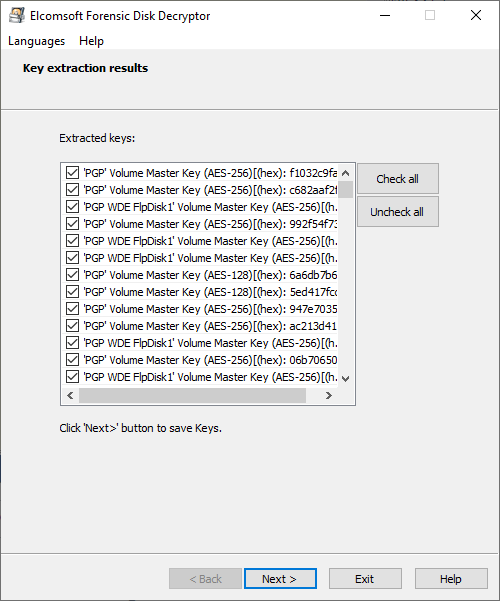
Please note that the encrypted disk should be mounted to the system when you make the dump (or when the computer has been put to the hibernate state); otherwise, the keys are not stored in the memory.
Searching for keys is a time-consuming process, so it is recommended to limit the search to particular key types.